|
A. Baumgrass, M. Strembeck:
Bridging the Gap between Role Mining and Role Engineering
via Migration Guides,
In: Information Security Technical Report (ISTR), Vol. 17, No. 4, May 2013
(doi,
pdf) |
 |
M. Leitner, A. Baumgrass, S. Schefer-Wenzl, S. Rinderle-Ma, M. Strembeck:
A Case Study on the Suitability of Process Mining to Produce Current-State
RBAC Models, In: Proc. of the Workshop on Security in Business Processes
(SBP), Lecture Notes in Business Information Processing (LNBIP), Vol. 132,
Springer, Tallinn, Estonia, September 2012
(ps,
pdf) |
 |
A. Baumgrass, M. Strembeck:
An Approach to Bridge the Gap between Role
Mining and Role Engineering via Migration Guides, In: Proc. of the 7th
International Conference on Availability Reliability and Security (ARES),
Prague, Czech Republic, IEEE, August 2012
(ps,
pdf) |
 |
A. Baumgrass, S. Schefer-Wenzl, M. Strembeck:
Deriving Process-Related RBAC Models from Process Execution
Histories, In: Proc. of the 4th IEEE International Workshop
on Security Aspects in Processes and Services Engineering (SAPSE),
Izmir, Turkey, July 2012
(ps,
pdf,
extended version) |
 |
A. Baumgrass, T. Baier, J. Mendling, M. Strembeck: Conformance Checking of
RBAC Policies in Process-Aware Information Systems,
In: Proc. of the Workshop on Workflow Security Audit and Certification (WfSAC),
Lecture Notes in Business Information Processing (LNBIP), Vol. 100, Springer Verlag,
Clermont-Ferrand, France, August 2011
(ps,
pdf) |
 |
W. Hummer, P. Gaubatz, M. Strembeck, U. Zdun, S. Dustdar: An
Integrated Approach for Identity and Access Management in a SOA Context,
In: Proc. of the 16th ACM Symposium on Access Control
Models and Technologies (SACMAT), Innsbruck, Austria, June 2011
(ps,
pdf) |
 |
A. Baumgrass, M. Strembeck, S. Rinderle-Ma: Deriving Role
Engineering Artifacts from Business Processes and Scenario Models,
In: Proc. of the 16th ACM Symposium on Access Control
Models and Technologies (SACMAT), Innsbruck, Austria, June 2011
(ps,
pdf,
extended version) |
 |
M. Strembeck, J. Mendling: Modeling Process-related RBAC Models
with Extended UML Activity Models,
In: Information and Software Technology, Vol. 53, No. 5, May 2011
(doi,
pdf) |
|
 |
M. Strembeck, J. Mendling: Generic Algorithms for Consistency Checking of
Mutual-Exclusion and Binding Constraints in a Business Process Context,
In: Proc. of the 18th International Conference on Cooperative Information Systems
(CoopIS), Lecture Notes in Computer Science (LNCS), Vol. 6426, Springer Verlag,
Crete, Greece, October 2010
(ps,
pdf,
extended version) |
|
 |
S. Kunz, S. Evdokimov, B. Fabian, B. Stieger, M. Strembeck: Role-Based Access
Control for Information Federations in the Industrial Service Sector
In: Proc. of the 18th European Conference on Information Systems (ECIS), Pretoria,
South Africa, June 2010
(ps,
pdf) |
|
 |
M. Strembeck: Scenario-Driven Role Engineering,
In: IEEE Security & Privacy, Vol. 8, No. 1, January/February 2010
(doi,
pdf) |
|
 |
J. Mendling, K. Ploesser, M. Strembeck: Specifying Separation of Duty
Constraints in BPEL4People Processes, In: Proc. of the 11th International
Conference on Business Information Systems (BIS), Lecture Notes in Business
Information Processing (LNBIP), Vol. 7, Springer Verlag, Innsbruck, Austria, May 2008
(ps,
pdf) |
|
 |
G. Stermsek, M. Strembeck, G. Neumann: A User Profile Derivation Approach based on
Log-File Analysis, In: Proc.of the International Conference on Information and
Knowledge Engineering (IKE), Las Vegas, NV, USA, June 2007
(ps,
pdf) |
|
 |
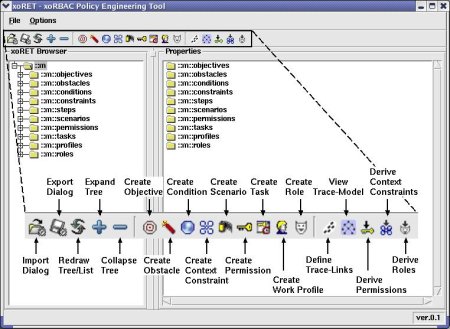
M. Strembeck: A Role Engineering Tool for Role-Based Access Control,
In: Proc. of the 3rd Symposium on Requirements Engineering for Information
Security (SREIS), Paris, France, August 2005
(ps,
pdf) |
|
 |
M. Strembeck:
Embedding Policy Rules for Software-Based Systems in a Requirements Context,
In: Proc. of the 6th IEEE International Workshop on Policies for Distributed
Systems and Networks (POLICY), Stockholm, Sweden, June 2005
(ps,
pdf) |
|
 |
M. Strembeck, G. Neumann:
An Integrated Approach to Engineer and Enforce Context Constraints in
RBAC Environments, In: ACM Transactions on Information and System
Security (TISSEC), Vol. 7, No. 3, August 2004
(doi,
pdf) |
|
 |
J. Mendling, M. Strembeck, G. Stermsek, G. Neumann:
An Approach to Extract RBAC Models from BPEL4WS Processes,
In: Proc. of the 13th IEEE International Workshops on Enabling Technologies:
Infrastructures for Collaborative Enterprises (WETICE), Modena, Italy,
June 2004 (ps,
pdf) |
|
 |
G. Neumann, M. Strembeck: A Scenario-driven Role Engineering
Process for Functional RBAC Roles, In: Proc. of 7th ACM Symposium
on Access Control Models and Technologies (SACMAT), Monterey, USA,
June 2002 (ps, pdf) |
|